
One of the cybercrime groups that attacked thousands of organizations around the world in the framework of a large-scale phishing campaign, forgot to hide stolen confidential data from search engines.
Information security specialists from Check Point and Otorio, who were engaged in researching a phishing campaign, found out that cybercriminals accidentally uncovered stolen credentials.
The report describes that hackers after theft of confidential information redirected it to domains that were registered specifically for storing stolen data. But all the stolen credentials were placed in a publicly available file, which was successfully indexed by Google.

Due to this, the search engine displays the results on the requests of the Email or password stolen address.
Security researchers from CHECK POINT and OTORIO noted that the Legal WordPress Legal Servers were also hacked, on which the PHP malicious page was posted, the link to which was sent to victims. "Usually, hackers prefer to use pre-compromised servers instead of their own infrastructure due to the high reputation of already existing sites," said Check Point experts.
Hackers used several compressed letters that were sent by victims to lure those on the transition to the target malware, which required the Microsoft Office 365 password and password. In the e-mail theme line indicated the name of the victim, the name of his company. Hackers did so that the victim seemed that she would receive an Xerox scanning letter in HTML format.
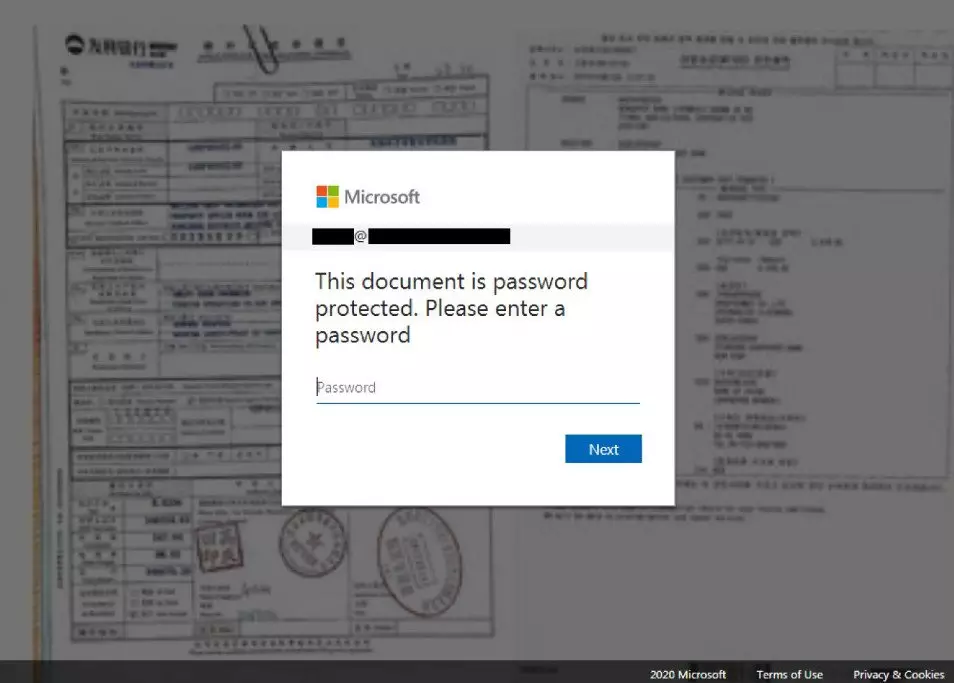
When opening an allegedly scanned file, the web browser has shown the blurred image to which a fake login form in Microsoft Office 365 is superimposed. It is interesting that the field where you need to enter the username was already filled with the email address of the victim, which further introduced it to misconception.
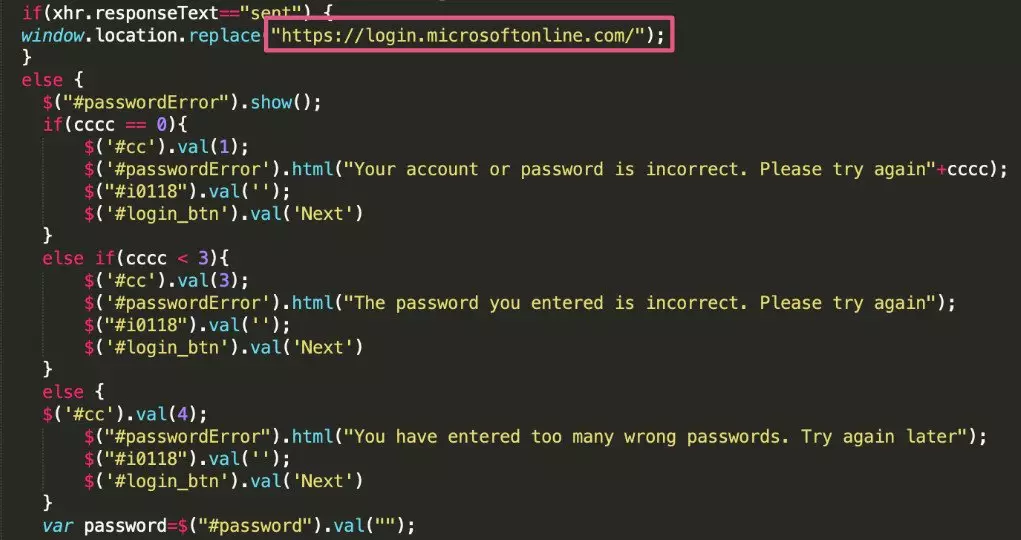
The javascript code, which works in the background, checked the reality of credentials, sent them to the cybercriminator server, after which it automatically redirected the victim to the present page of the authorization in Microsoft Office 365 to take all suspicions in phishing.
Although this phishing campaign began in August 2020, researchers from Check Point and Otorio discovered phishing letters from the same cybercrime group dated by May 2020. Google does not first index pages on which hackers publish stolen. This shows that not all attackers have sufficient qualifications to protect the results of their operations.
More interesting material on cisoclub.ru. Subscribe to us: Facebook | Vk | Twitter | Instagram | Telegram | Zen | Messenger | Icq new | YouTube | Pulse.
