
Each day throughout the country, digitalization covers an increasing number of production processes: at industrial enterprises, in the banking sector, in the branches of science and medicine, Internet sphere and communications, and many others. However, there are also significant risks associated with information security in parallel with explicit benefits. The growth of hacker attacks on industrial systems is a global trend, and one antiviruses with cybercrime definitely not to cope.
How to protect the inviolability of information systems and infrastructures, told during a special training webinar organized by Rostelecom and Schneider Electric. A journalist of the Novosibirsk Publication of NDNFO also became a member of the webinar.
The theme of the webinar was the information security of industrial facilities and critical infrastructure. At the meeting, the Schneider Electric cybersecurity consultant was performed at Andrei Ivanov, who managed to present a full picture of possible risks relating to this sphere, and "decomposed on the shelves" options for protection.
What is ACS TP?
First of all, the speaker explained that it was an ACS TP (automated technological process control system). This is a group of solutions of technical and software intended for automation of technological equipment management at industrial enterprises.This system represents: field devices, process management tools, as well as factory systems.
In the first case, these are a different kind of sensors and devices that convert the physical characteristics of technoprocesses into digital information (temperature measurement, pressure, electricity distribution, etc.)
In the second, we are talking about police envisions that can conduct calculations and process information, such as programmable logic controllers.
In the third - information systems in enterprises that use data from the lower levels to make decisions based on their basis, reporting and other tasks.
Cybercrime: Getting from the 70s
Personal computers first appeared in the 70s of the last century. And although it was extremely few of them, the first hackers appeared almost immediately, and as the result - the first viruses and attempts to theft of information. So in 1974, the concept of "information security" was formulated, which includes the protection of the analog and new ones at that time of digital information.
Cybersecurity is a term already today, its task is to protect both directly digital information and other objects that become vulnerable through ICTs (information and communication technologies).

Access to the system
The first question that occurs in a person who is not immersed in this subject - why to protect the ACS TP? There are no financial information in them, the systems themselves are isolated. However, everything is not so simple."As a rule, the ACS systems of TP are connected to the ASUP systems (enterprise management) and one way or another shall be exchanged with them. And the ASUP system is located in the corporate network, which has access to the Internet, is first. And secondly, there is such a concept as an internal violator: you can bribe, intimidate, blackmailing an employee who has legal access to the ACS TP system, "explained Andrei Ivanov.
Therefore, this question is very important. Thus, Rostelecom-Sollar in 2020 recorded that 40% of hacker attacks account for servers and workstations of technological processes.
Sugagable reliable protection
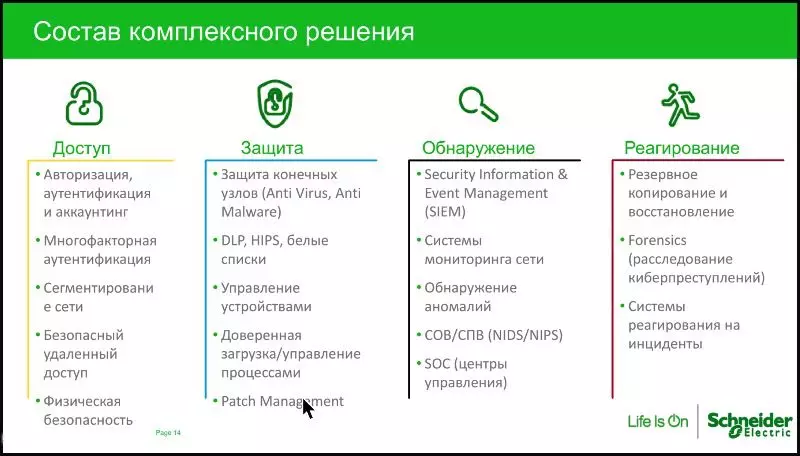
What will help to establish the security of an automated control system? The presenter of the webinar divided the components of the protection system into four directions:
- Access control control (physical security, authorization, authentication, etc.);
- Protection (antivirus system, devices management, etc.);
- Detection (network monitoring system, detection of anomalies, etc.);
- Response (response tools, backup and recovery, etc.).
In turn, the levels of protection are also different and aimed at protecting end nodes (anti-virus software, control of connected devices), network protection (detecting unauthorized attempts to dacha commands) and the protection of the components of the ACU TP (embedded functional).
However, only the introduction of these methods in the complex will allow preventing penetration into the system.
"Why is there so many different means of protection? Because today there is no universal solution, some silver bullets from the box, acquiring which and installing on ACS TP, we can assume that they are protected from everything, "Andrei Ivanov focused.
A set of measures to protect topics and effective that even if an attacker can overcome some one or even two levels, others will stop.
Cybersecurity in Russia
In our country, the protection of the ACS TP regulates the Federal Law "On the Safety of Critical Information Infrastructure of the Russian Federation", he began to act from January 1, 2018. It includes 12 industries that must be protected in obligatory. Hope on "Avos" in this case should not be exactly, even if the protection measures will require significant investment.
"Security incidents will be inevitable. Without any "maybe", "if", "when", "under the condition". It will happen, and it is necessary to be ready for this, "Andrei Ivanov resums.
Read other interesting materials on NDN.info
