Why developers are difficult to monetize their projects and how to avoid the installation of malicious extensions.
Kybersecurity Specialist Brian Krebs disassembled the market of extensions for the browser and the methods of their monetization. He came to the conclusion that setting even popular extensions with hundreds of thousands of users can be dangerous due to their business model.
In his publication, Krebs talks about the Singapore company Infatica with the Russian founder Vladimir Fomenko. Infatica provides web proxy services in an unusual way: the company negotiates with the expansion developers, so that the Infatica proxy code in their projects imperceptibly integrated.
As a result, the infatica client traffic router is running through the user's browser, in return, the developer receives a fixed payment from $ 15 to $ 45 for each thousand active users.
Infatica is only one in the growing industry of shadow firms that are trying to cooperate with the developers of popular extensions and use their development for their own purposes. The developers are forced to agree to at least somehow recoup the costs of extension support, Krebs notes.
How the economy is arranged between extensions and infatica
Some extensions for Apple's browsers, Google, Microsoft and Mozilla collect hundreds of thousands, and even millions of active users. As the audience grows, the expansion author may not cope with the project support - its updates or answers to user requests.
At the same time, to obtain financial compensation for their works in authors a little - a subscription can scare away, and Google announced the closure of paid extensions in the Chrome store.
Therefore, sometimes the extension for the author becomes either a complete sale of expansion, or hidden integration of someone else's code. "This offer is often too attractive to refuse it," Krebs writes.
For example, this was done by the developer of expansion for testing MODHEADER sites Hao Nguyen, which is used by more than 400 thousand people.
When Nguyen realized that he spends more and more money and time to support Modheader, he tried to include advertising in extension, but after a large protest, he had to give up this. Moreover, the advertisement did not bring him a lot of money.
"I will spend at least 10 years to create this thing, and I failed to monetize it," the Nguyen recognizes. Partially he blames Google for closing paid extensions - according to him, it only aggravated the problem of disappointed developers.
Nguyen himself initially abandoned several offers of companies offering to pay for the integration of their code into expansion, as they would receive complete control over the work of the browser and user devices at any time.
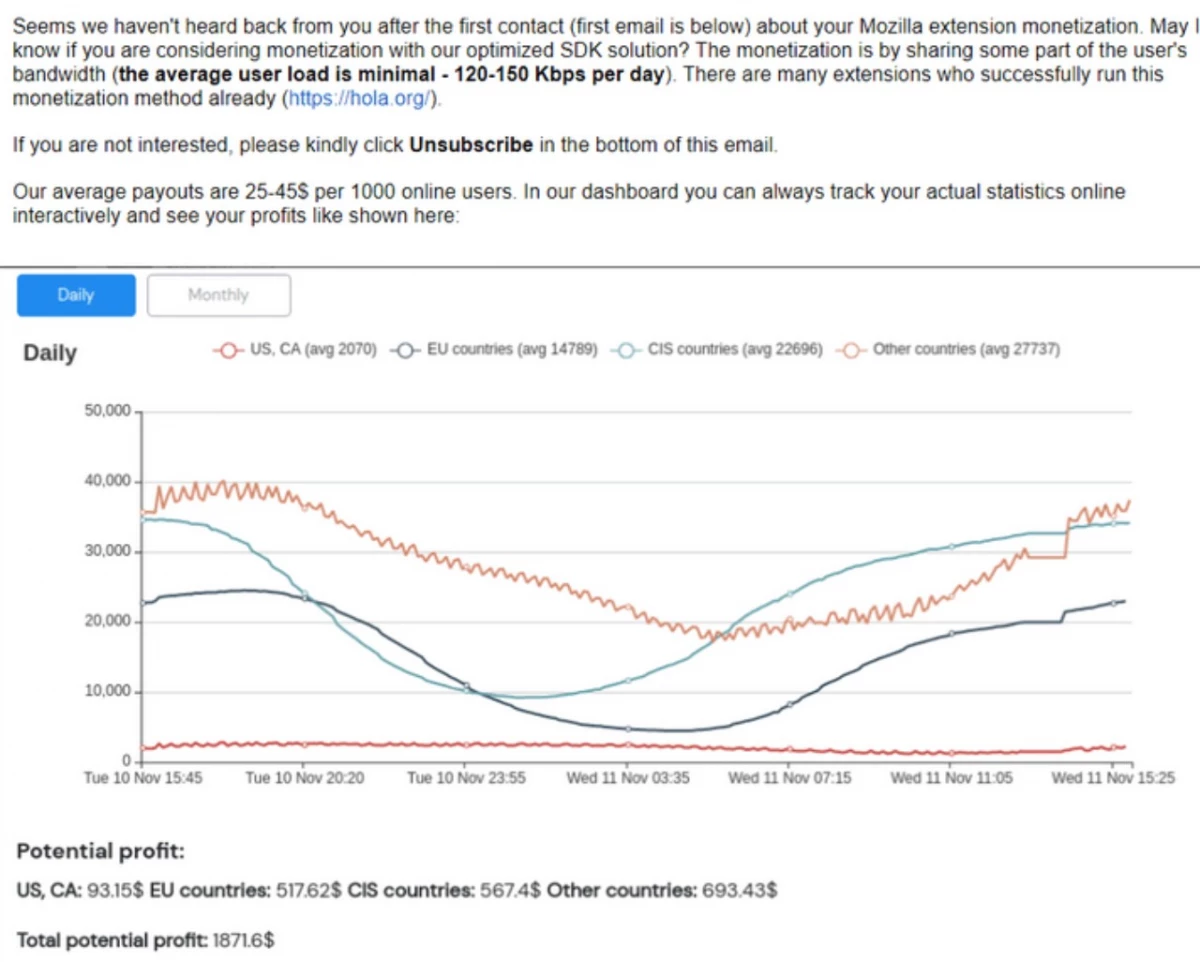
Infatica code was simpler - they were limited to the routing of requests without access to saved user passwords, reading their cookie or view the user's screen. In addition, the transaction would bring Nguen at least $ 1500 per month.
He agreed, but in a few days he received many negative user reviews and deleted Infatica code. In addition, the expansion began to use to view "not very good places, such as porn," notes by Modheader.
The infatica chapter owns the Ininja VPN VPN service with an audience of 400 thousand users. It also uses the same systems to routing traffic - an extension for Chrome and the same-named advertising blocker, which contains Infatica.
Infatica is similar to HolavPN - VPN service with a browser extension. In 2015, cybersecurity researchers found that those who had established the HOLA extension were used to redirect traffic other people.
INFATICA marketing team just compares its business model with the HolavPN model, notes Krebs.
How big is the extension market
The second project of NGUEN - the service of statistics of Chrome-stats.com, which contains information about more than 150 thousand extensions, the extended version of the service is offered by subscription.
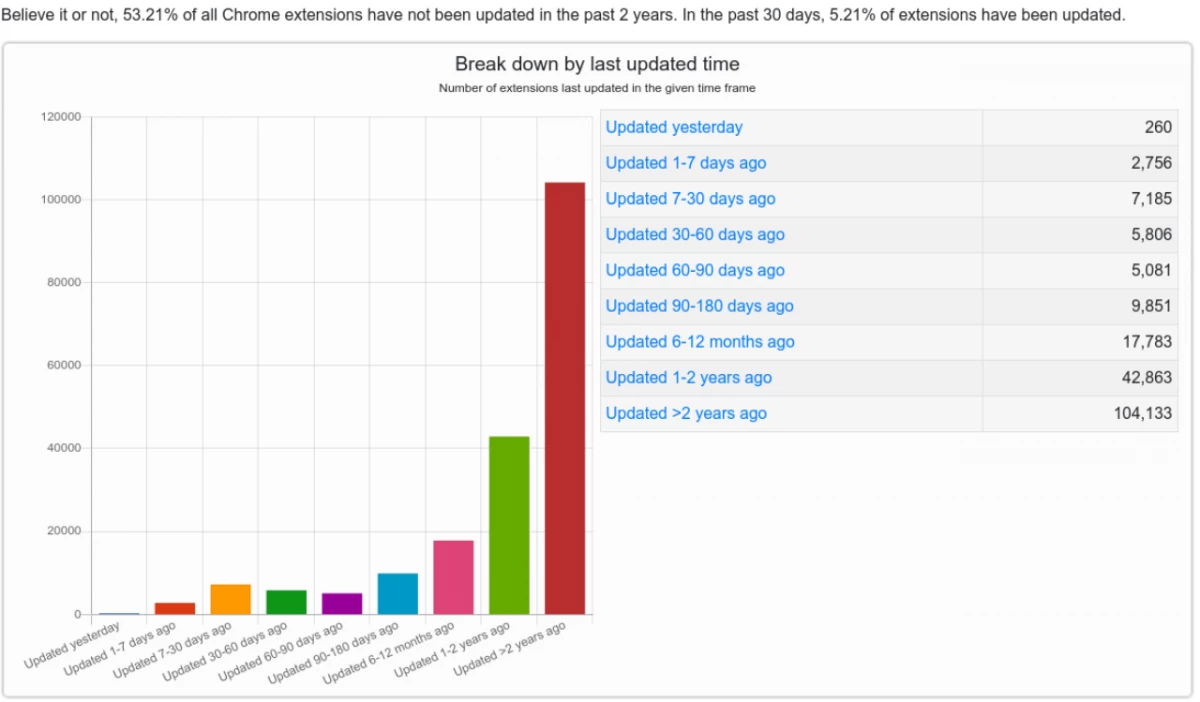
According to Chrome-Stats, more than 100 thousand extensions are abandoned by the authors or have not been updated for more than two years. This is a significant reservoir of developers who may well agree to sell their project and its custom base concludes Krebs.
How many extensions use the Infatica code Unknown - Krebs found at least three dozen, several of them had more than 100 thousand users. One of them is Video Downloader Plus, the audience of which was at the peak of 1.4 million active users.
How not to get to malicious expansion
The permissions of each expansion are spelled out in its "Manifesto" - the description is available during its installation. According to Chrome-Stats, about a third of all Chrome extensions do not require special permits, but the rest require complete confidence from the user.
For example, about 30% of extensions can view user data on all or specific sites, as well as index open tabs and perfect actions on web pages. 68 thousand extensions can perform arbitrary code on the page by changing the functionality or appearance of the site.
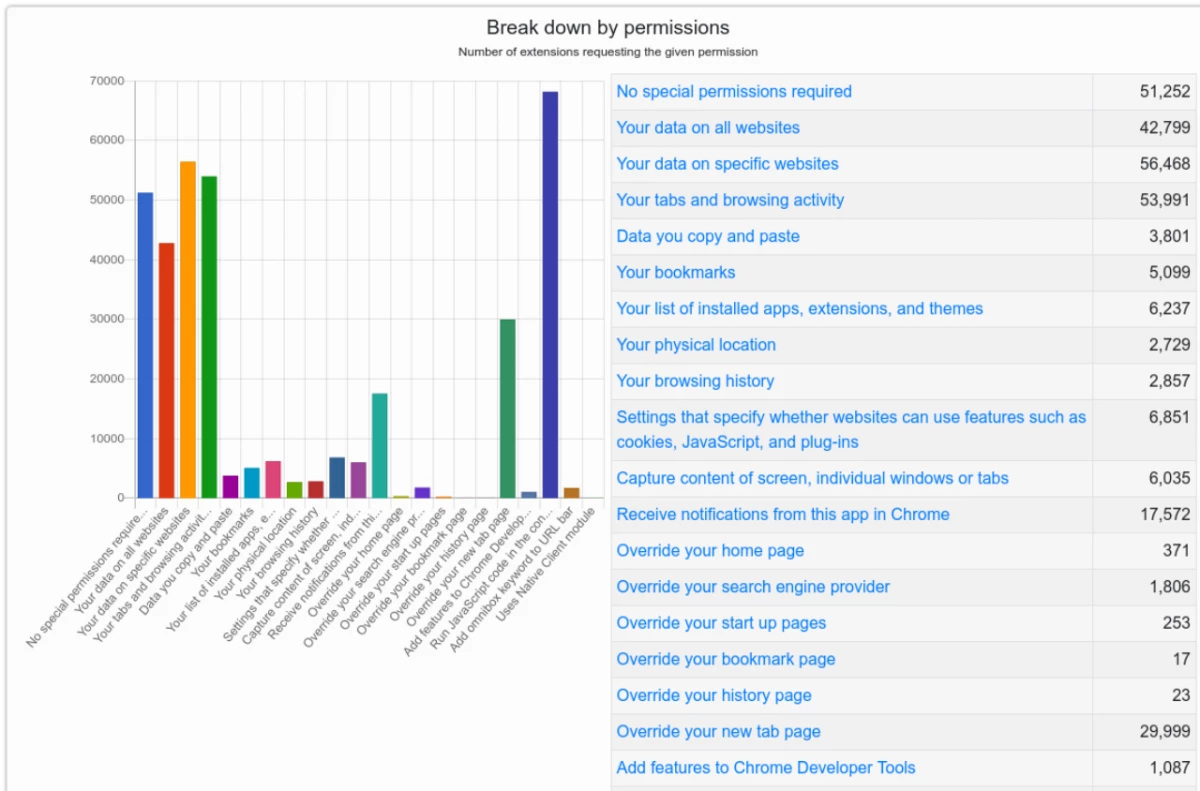
When installing extensions, you need to be extremely careful and choose those that are actively supported by the authors and respond to user questions, Krebs believes.
If the extension asks to upgrade and suddenly requests more permits than before - this is a reason to think that something is wrong with him. If this expansion had full access, Krebs recommends completely removing it.
Also, you can also load and set an extension, because the site is written that it is necessary to view some content - it almost always means a big risk, notes a cybersecurity specialist.
And you always need to stick to the first network security rule: "If you did not look for it, then do not install."
# Browsers Extensions
A source
